The Lightweight Directory Access Protocol (LDAP) is an application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. More info about LDAP.
- Download Apache Directory Studio (ADS) Tutorial created with 2.0.0 version.
- Run ADS.
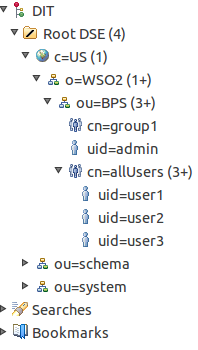
- Lets assume that we need to create a LDAP structure looks like below example
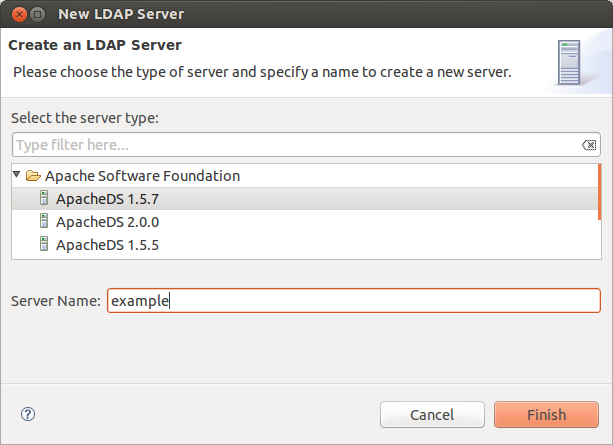
- First you have to create a LDAP server
- In ADS window at bottom left corner, go to LDAP servers tab right click inside the panel > New > New server.
- Select the server version, enter a name and click finish to create the server.
- You will see the new server at the LDAP servers list.
- Now if you observe the structure that we are going to create, it starts with the root c=US.
- In-order to do this we have to create a partition with the suffix c=US inside the server we created.
- Right click on the server we created in LDAP server list (caption 2) and click Open Configuration
- In the opened server.xml file, go to the partition section by clicking the partition tab at the bottom of the page.
- Click add button and give a name to ID and set the suffixc=US.
- Save the settings (ctrl+s).
- Now go to LDAP server list (caption 2). Right click on the server and click Run.
- Again right click on the server and click Create a connection.
- Go to the Connections tab (next to the LDAP servers tab , caption 2)
- You will see a new connections has been created with the server name.
- Double click on the new created connection. It will open the LDAP structure in the LDAP browser.
- Now we can start creating the LDAP structure.
- First we'll create the country inside the root.
- Right click on the Root in LDAP Browser and click New > New Entry...
- In the new window select Create entry from scratch and click Next.
- Form the Available object classes select Country and by clicking the Add button add it to the Selected object classes. Click Next.
- Note that it will add the dependent objects automatically. Do not remove them.
- Keep the parent empty since this will be the root and fill RDN values c and US.
- Click Next and then click Finish.
- You will now see the c=US root element in the LDAP browser.
- Now let's create the organization unit as BPS.
- Right click on the o=WSO2 element in LDAP Browser and click New > New Context Entry...
- In the new window select Create entry from scratch and click Next.
- Form the Available object classes select OrganizationalUnit and by clicking the Add button add it to the Selected object classes. Click Next.
- Note that it will add the dependent objects automatically. Do not remove them.
- For the DN pattern enter ou=BPS,o=WSO2,c=US and click Next and Finish.
- Now we can add the admin user to BPS.
- Right click on the ou=BPS element in LDAP Browser and click New > New Context Entry...
- In the new window select Create entry from scratch and click Next.
- Form the Available object classes addOrganizationalPerson, uidObject to the Selected object classes. Click Next.
- Note that it will add the dependent objects automatically. Do not remove them.
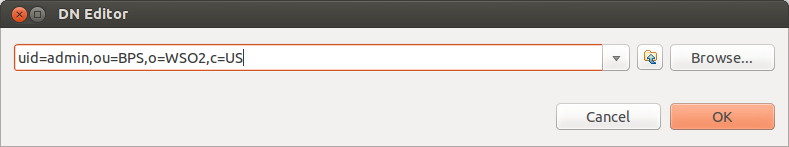
- For the DN pattern enteruid=admin,ou=BPS,o=WSO2,c=US and click Next.
- Set the same value admin to cn and sn by right clicking on those attributes and select Edit value.
- Click Finish after setting all the values as shown in the above caption.
- Note that we are unable to create groups without having at least one user. Now since we have at least one user created in the LDAP structure we can start creating groups.
- Right click on the ou=BPS element in LDAP Browser and click New > New Context Entry...
- In the new window select Create entry from scratch and click Next.
- Form the Available object classes add groupOfNames to the Selected object classes. Click Next.
- Note that it will add the dependent objects automatically. Do not remove them.
- For the DN pattern entercn=allUsers,ou=BPS,o=WSO2,c=US and click Next.
- There will be a new popup window asking to enter at-least one member to the group.
- Give the admin user DN patter (uid=admin,ou=BPS,o=WSO2,c=US) and click OK.
- Click Finish after setting all the values as shown in the above caption.
- Lets create another group named as group1.
- Right click on the ou=BPS element in LDAP Browser and click New > New Context Entry...
- In the new window select use existing entry as template and make sure it has mentioned the correct DN patter for the existing group allUsers. Click Next.
- Note that the objects has been already loaded to theSelected object classes since we are using the settings from allUser group. Click Next.
- For the DN pattern entercn=group1,ou=BPS,o=WSO2,c=US and click Next.
- Keep the rest of the settings as it is and click Finish.
- Now lets create some users in allUsers group.
- Right click on the uid=admin element in LDAP Browser and click New > New Context Entry...
- In the new window select use existing entry as template and make sure it has mentioned the correct DN patter for the existing user admin. Click Next.
- Note that the objects has been already loaded to theSelected object classes since we are using the settings from admin user. Click Next.
- For the DN pattern enteruid=user1,cn=allUsers,ou=BPS,o=WSO2,c=US and click Next.
- Set the same value user1 to cn and sn by right clicking on those attributes and select Edit value.
- Click Finish after setting all the values.
- Repeat the same steps to create more users. Create user2 and user3.
- Now lets add user2, user3 to group1.
- Click on the group1 from the LDAP browser. The settings will open in the right side window.
- Right click on the empty space and select New Attribute.
- In the new window set member for the attribute type and click Finish.
- In the new popup window enter the DN pattern for user1 as uid=user2,cn=allUsers,ou=BPS,o=WSO2,c=US.
- Repeat the above 4 steps to add user3 to group1 as well.
- Congratulations !! You have created the LDAP structure.
- After creating an LDAP structure, if you want to backup the data, you can always right click on the Root element in LDAP browser and select Export as a ldif file. Then next time you can Import them in the same way after creating the partition (c=US in this example) in the server with the suffix.